Deploy Your Own OpenVPN Server on AWS

After using Surfshark VPN and constantly experiencing their IP being blocked by Google reputation check, it sparked my interest to set up my own VPN server on AWS.
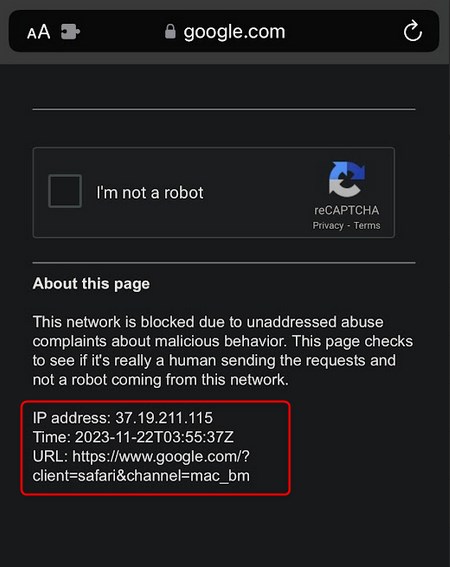
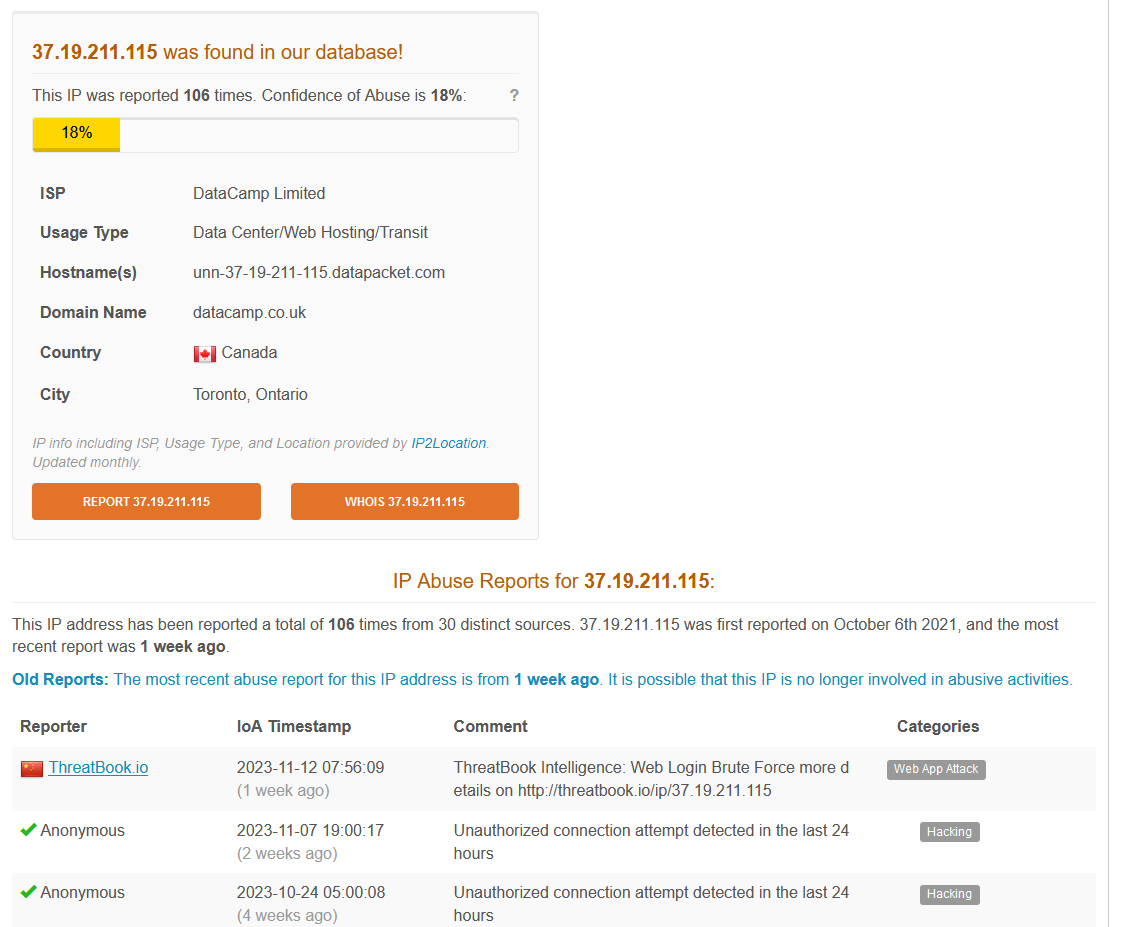
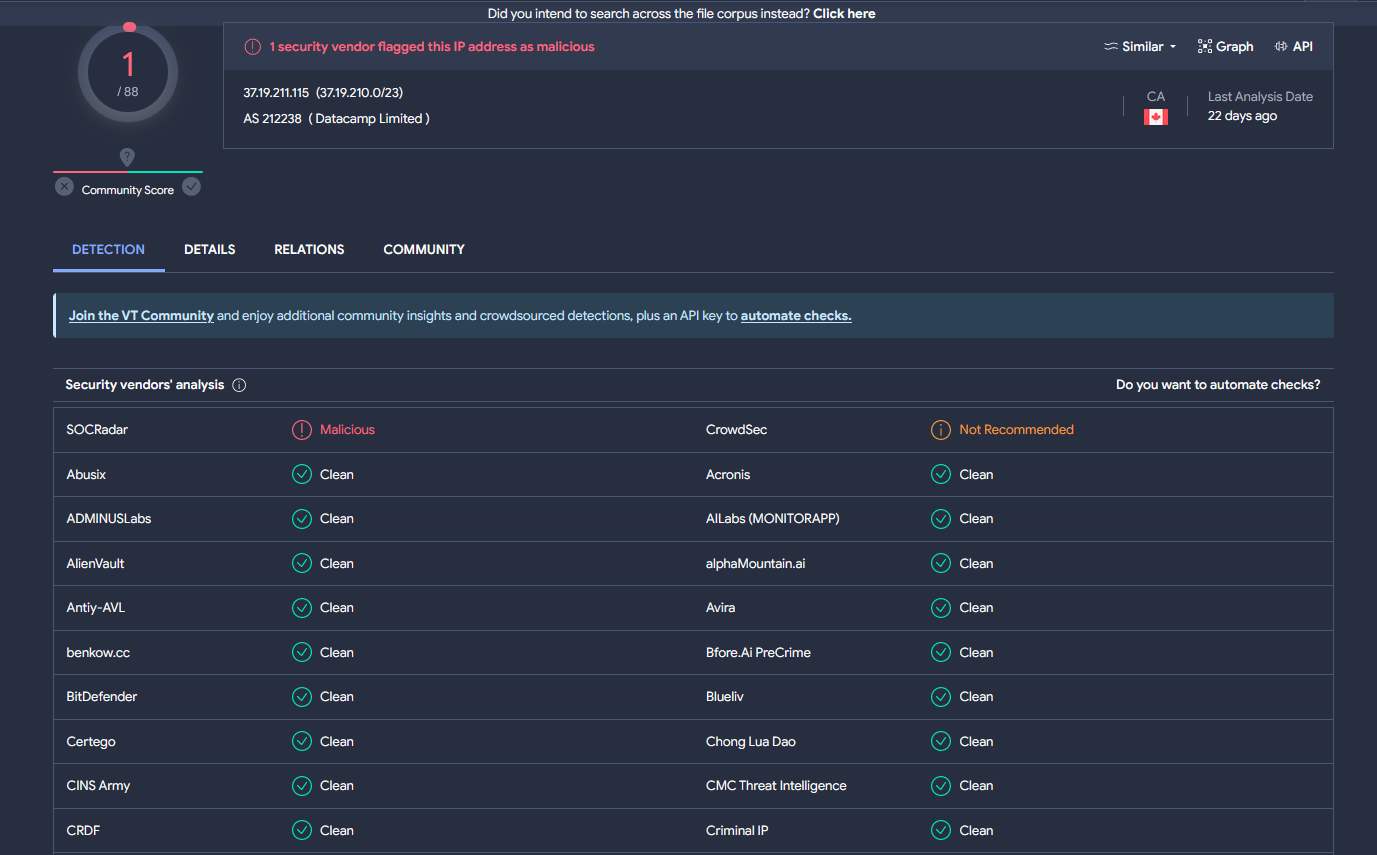
As you can see in the screenshot, the majority of the Surfshark IP runs on Datacamp which is constantly abused by bad actors to conduct nefarious activities across the internet and has a poor reputation. I ran the IP 37.19.211.115 that I connected to through AbuseIPDB and VirusTotal, and both returned negative results.
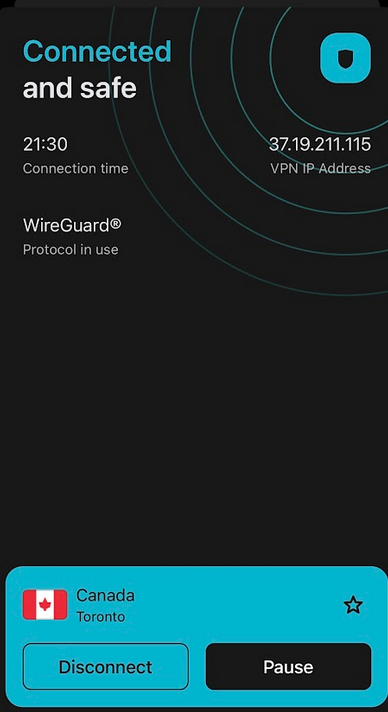
In this article, I will walk you through how to set up an OpenVPN access server on an AWS EC2 instance.
If this is your first time using AWS, you need to sign up for an account on aws.amazon.com. You will be logged in as an AWS root user however it’s the best practice to create a separate IAM account for day-to-day usage.
Here, since I am based in Canada, I will choose the “Canada ca-central-1” cloud region for the best VPN connection speed. But if you are located in another country, you can choose the cloud region that is closest to your location.
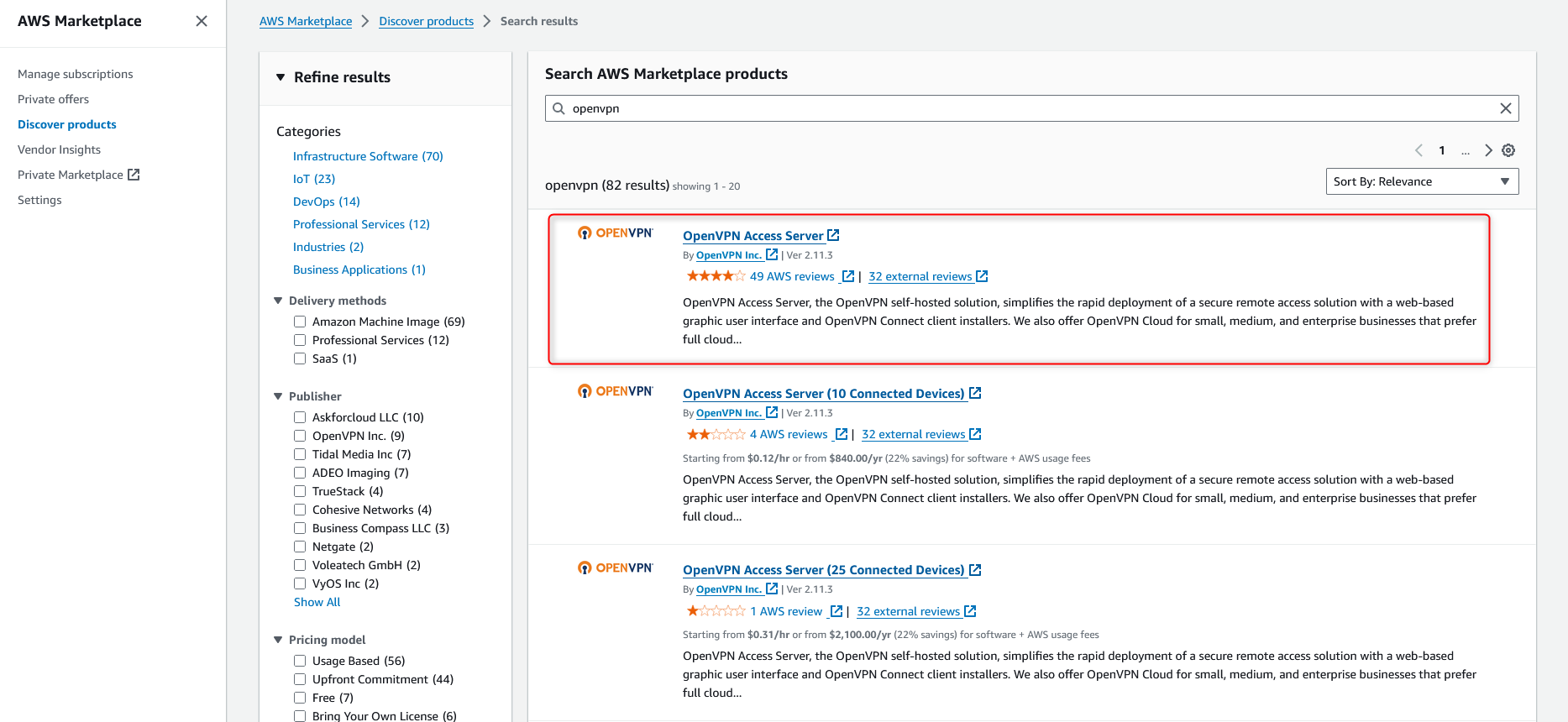
Next, let’s go to the AWS Marketplace and search for “OpenVPN” Amazon Machine Image. The first result “OpenVPN Access Server” is the result we are looking for.
Note that if you are a new user of AWS, you are eligible for 750 hours each month of free usage on a t2-micro instance which is the one we will use in this blog. You can find more information on the AWS free tier at here. Please also note that the OpenVPN Access Server provides two concurrent connections on their free tier, so for my use case, I will just stick with the free tier to keep from being charged.
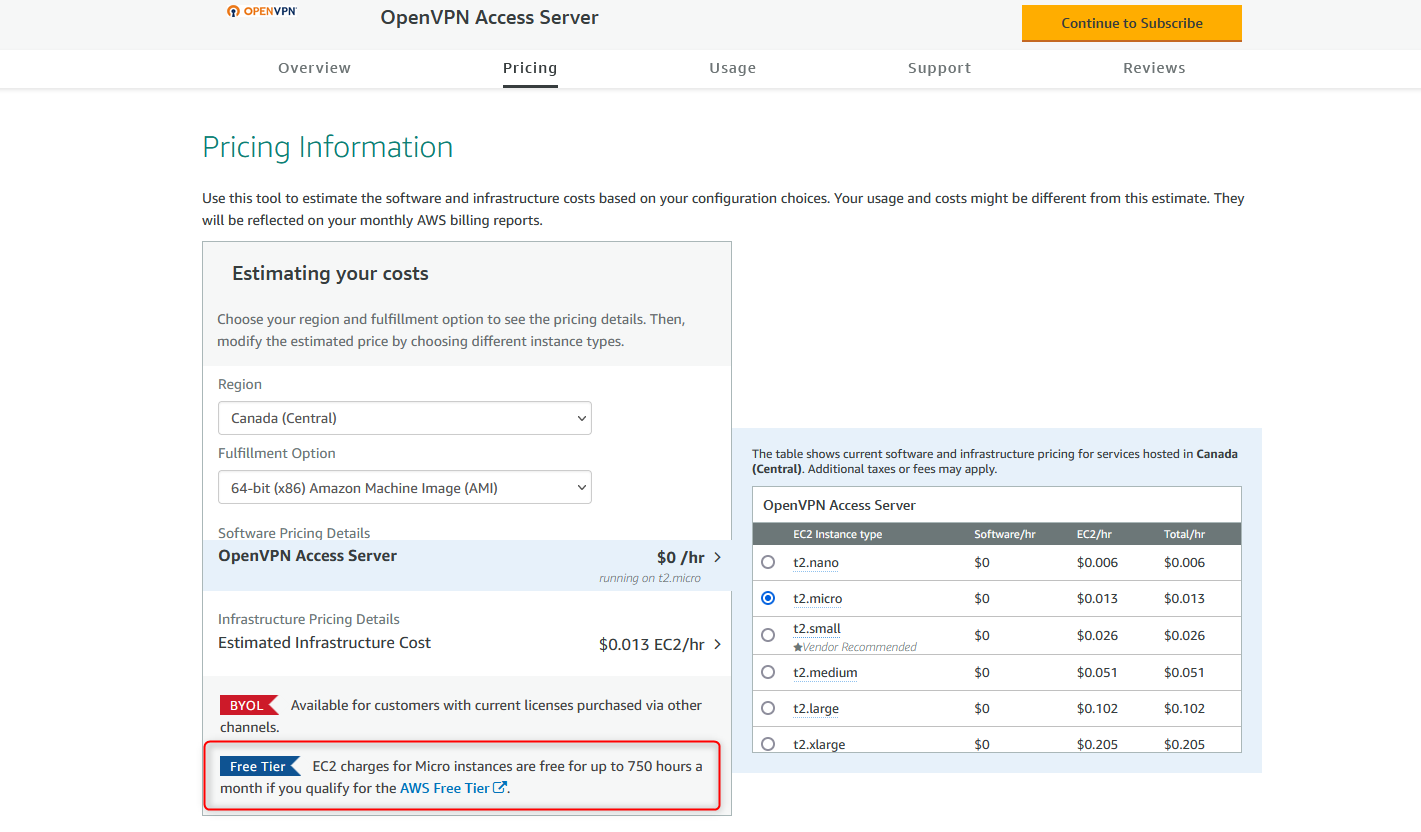
Next, let’s click on “Continue to Subscribe” with our OpenVPN Access Server then “Continue to Configuration”. Once you are on the “Configure this software” page, please choose the region that this EC2 instance should be launched, here I chose Canada. Then, go to “Continue to Launch”.
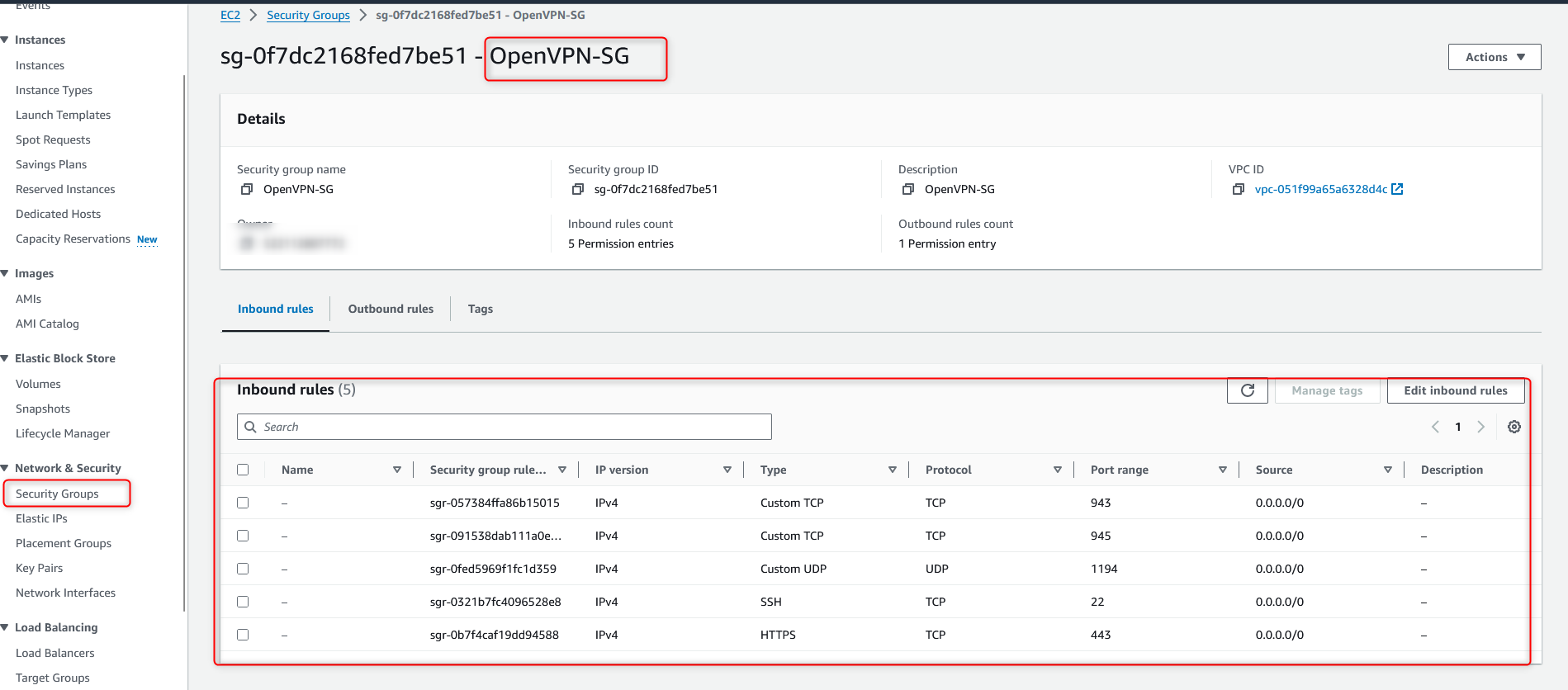
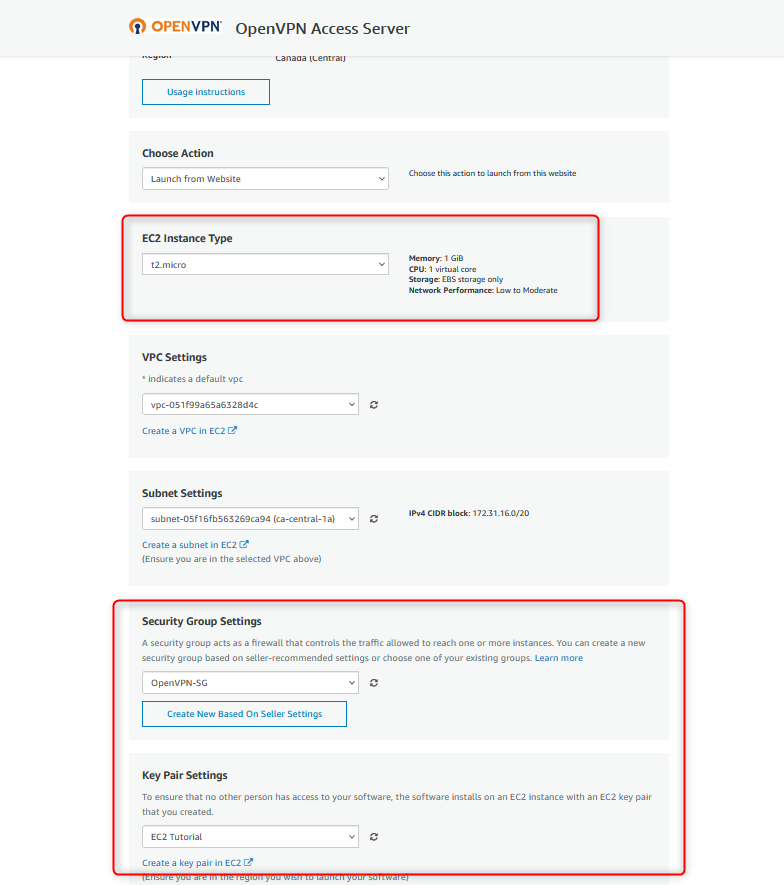
On the “Launch this software” page, change the “EC2 Instance Type” to “t2.micro” and “Security Group Settings” to the one OpenVPN has configured for you. I set the “Security Group” to the custom security group “OpenVPN-SG” I created earlier. Please refer to the OpenVPN official documentation with the following ports that need to be opened: https://openvpn.net/vpn-server-resources/amazon-web-services-ec2-byol-appliance-quick-start-guide/
For the security group, we recommend using the default group for the marketplace instance but adjusting the sources for some ports to improve security.
TCP 22: For SSH to remotely administer your appliance. We recommend you restrict this port to trust IP addresses by entering a specific subnet in CIDR notation (e.g., 12.34.56.0/24 for a subnet or 11.22.33.44/32 for a single IP address).
TCP 943: The Admin Web UI uses this port, which is also served on port 443 by default.
TCP 945: The clustering functionality uses this port. If you don’t use this feature, you don’t need to open this port. If you do, ensure the cluster nodes can reach each other on their public addresses.
TCP 443: For HTTPS, used by the Client Web UI, the interface where your users sign into the VPN server to retrieve client or config files. We recommend leaving this port open to the source as 0.0.0.0/0. The Admin Web UI is also default enabled on this port unless you turn off this setting. In multi-daemon mode, the OpenVPN TCP daemon shares this port with the Client Web UI, and your clients initiate TCP-based VPN sessions under this port number.
UDP 1194: For the OpenVPN UDP port used by your clients to initiate UDP-based VPN sessions to the VPN server, the preferred way for clients to communicate. Keep this port open for all clients.
If you want to further lock down the SSH access to your EC2 instance, you can set the SSH source to the specific IP range that is only allowed to connect from but here for simplicity, I will just use anywhere which is “0.0.0.0/0”.
If you want to SSH into the EC2 from your local machine, you also need to configure an SSH keypair and add it to the “Key Pair Settings”. I will use the key I have created earlier. Then, click on Launch.
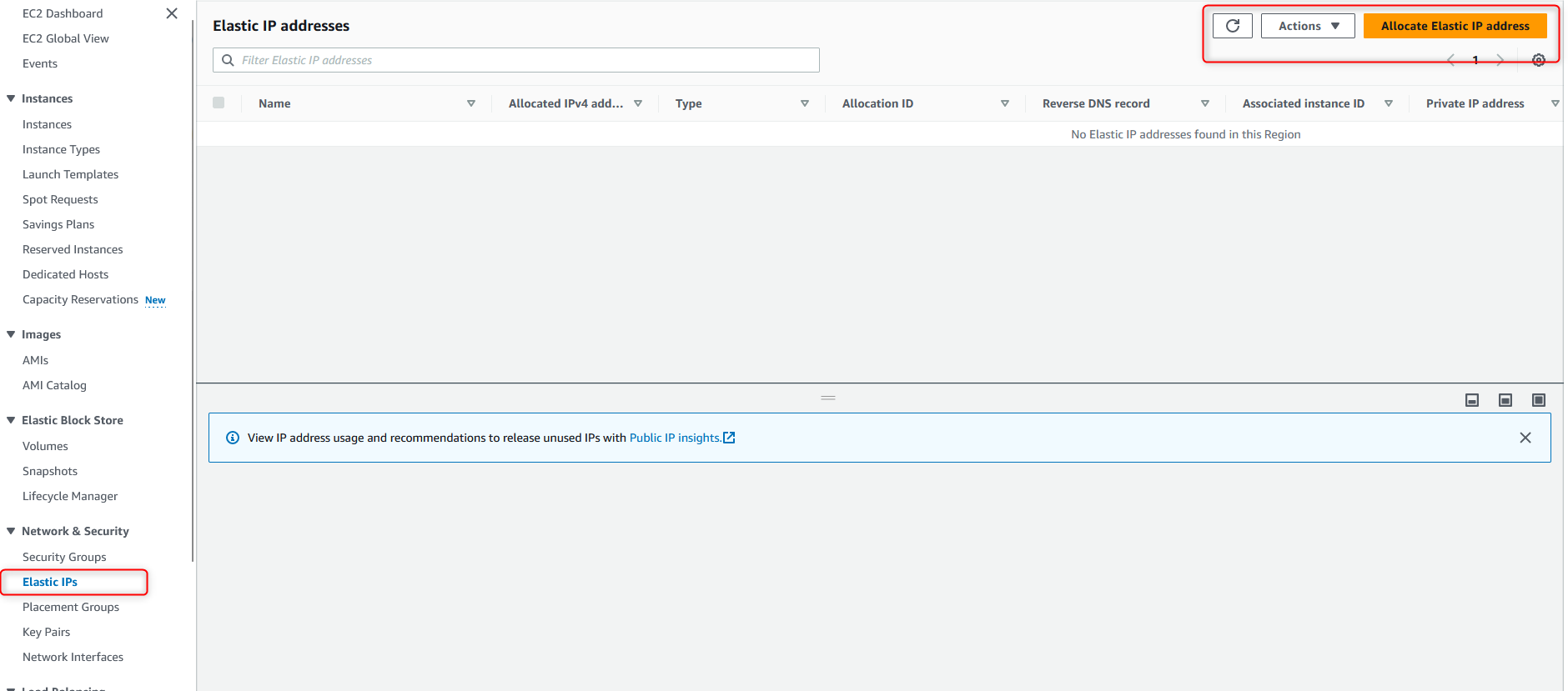
To ensure the EC2 instance to stays on a static IP, let’s create an “Elastic IP address” and associate it with the EC2 instance we just launched. Please note that there will be no charge incurred if your elastic IP is assigned to a running EC2 instance. However, if you decide to stop your EC2 instance, please make sure to delete your elastic IP to avoid being charged.
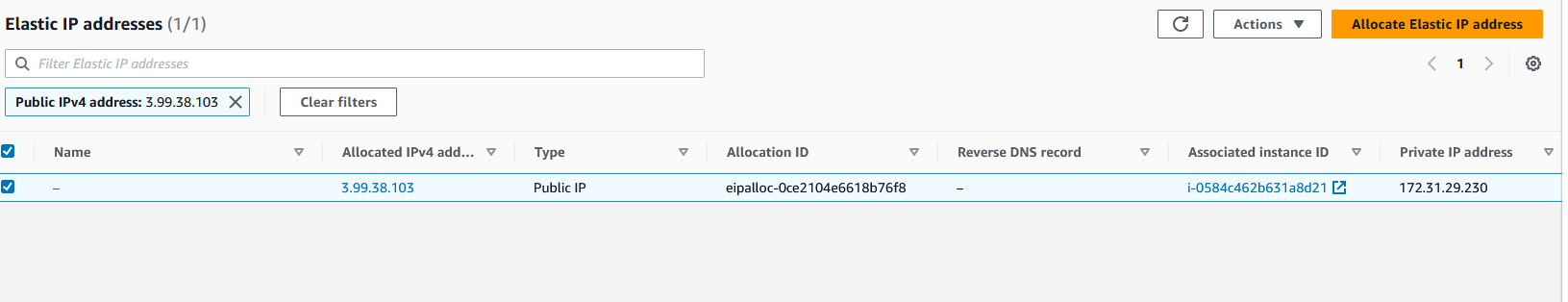
After I associate my elastic IP to my running EC2 instance, it will look like the following screenshot:
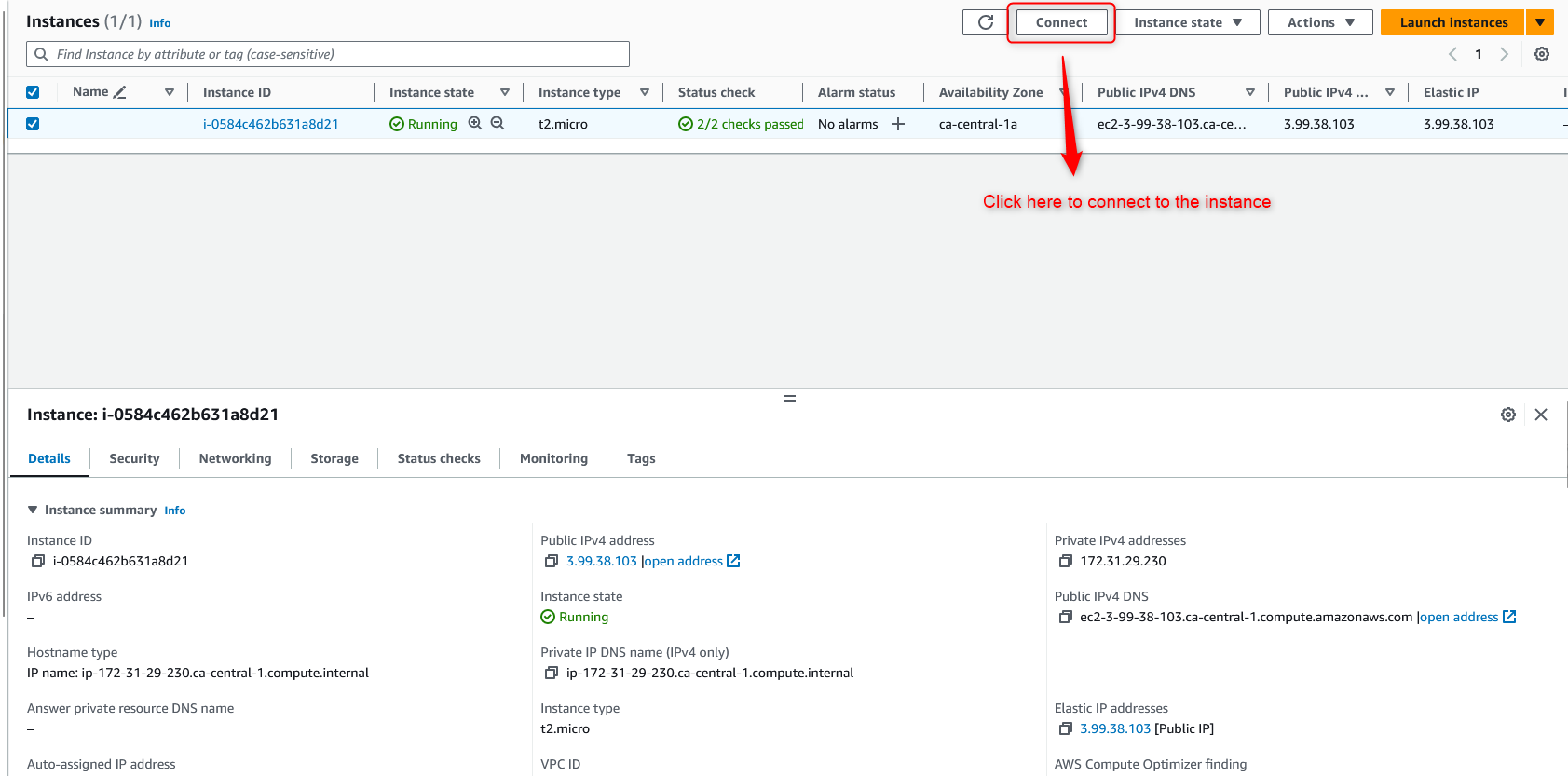
Now, let’s connect to the EC2 instance through the Amazon SSH connect, which is a browser-based SSH connection experience.
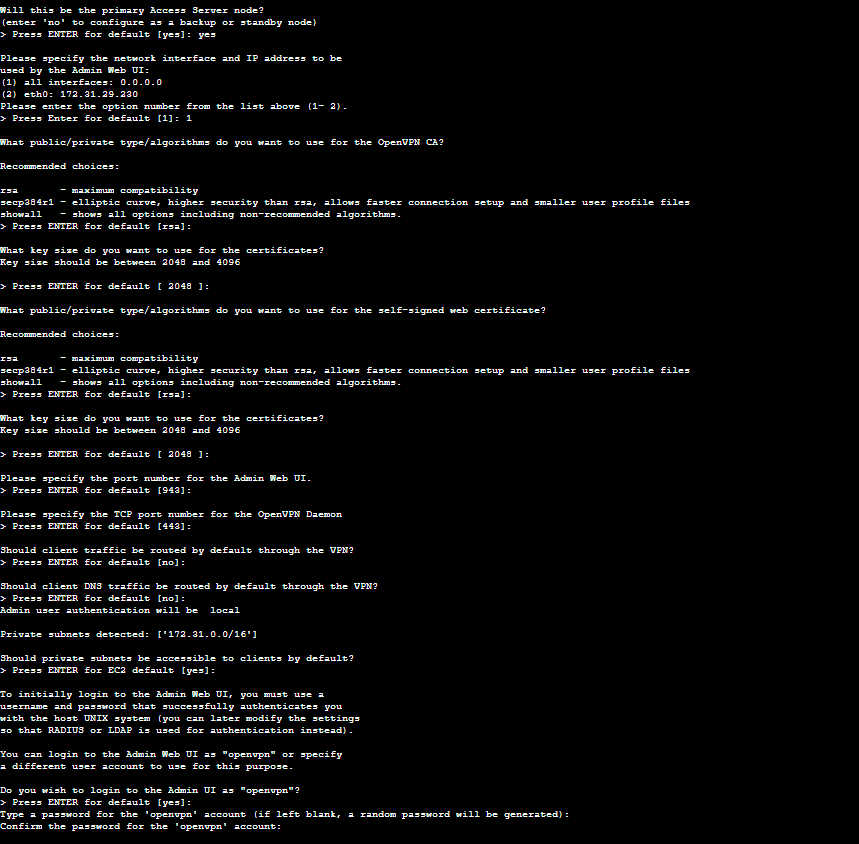
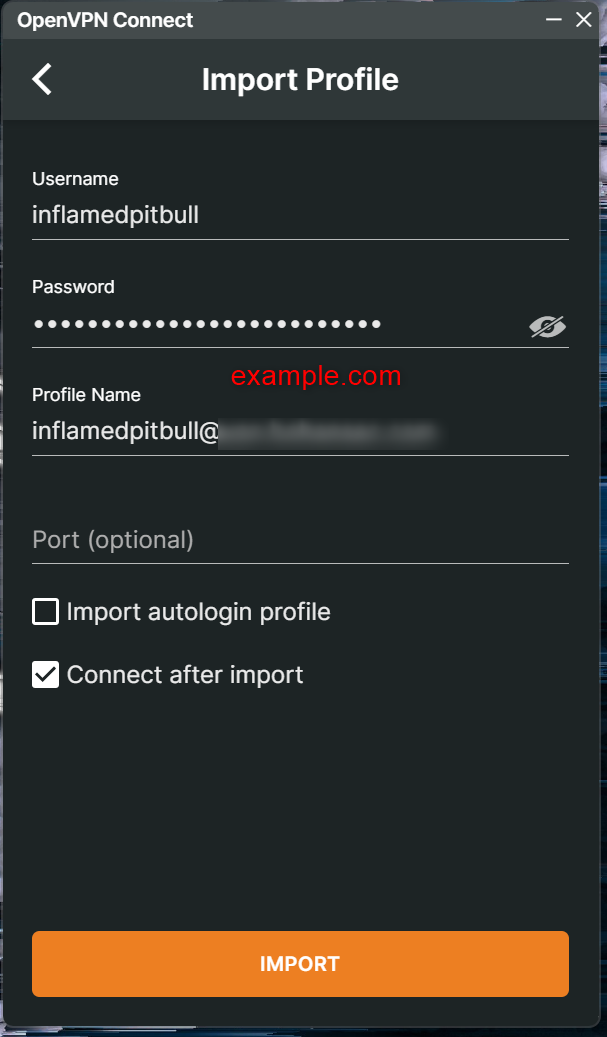
Once we connect to the server, for simplicity, enter Yes and Default to all of the prompts, also remember to configure a strong password for your Admin WebUI account. The default account will be “openvpn”.
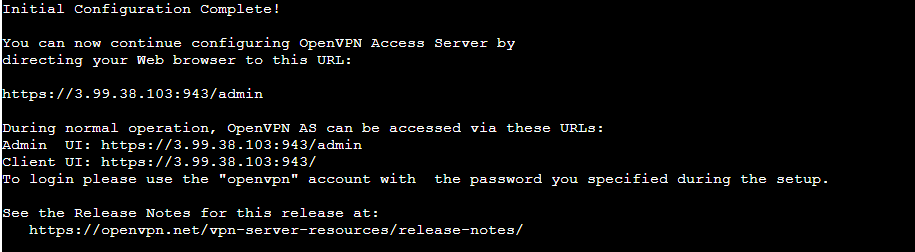
After the configuration is finished, we can see my Admin portal is located at “https://3.99.38.103:943/admin” but you may have a different IP address than mine so just use whatever public IP address you have to log in.
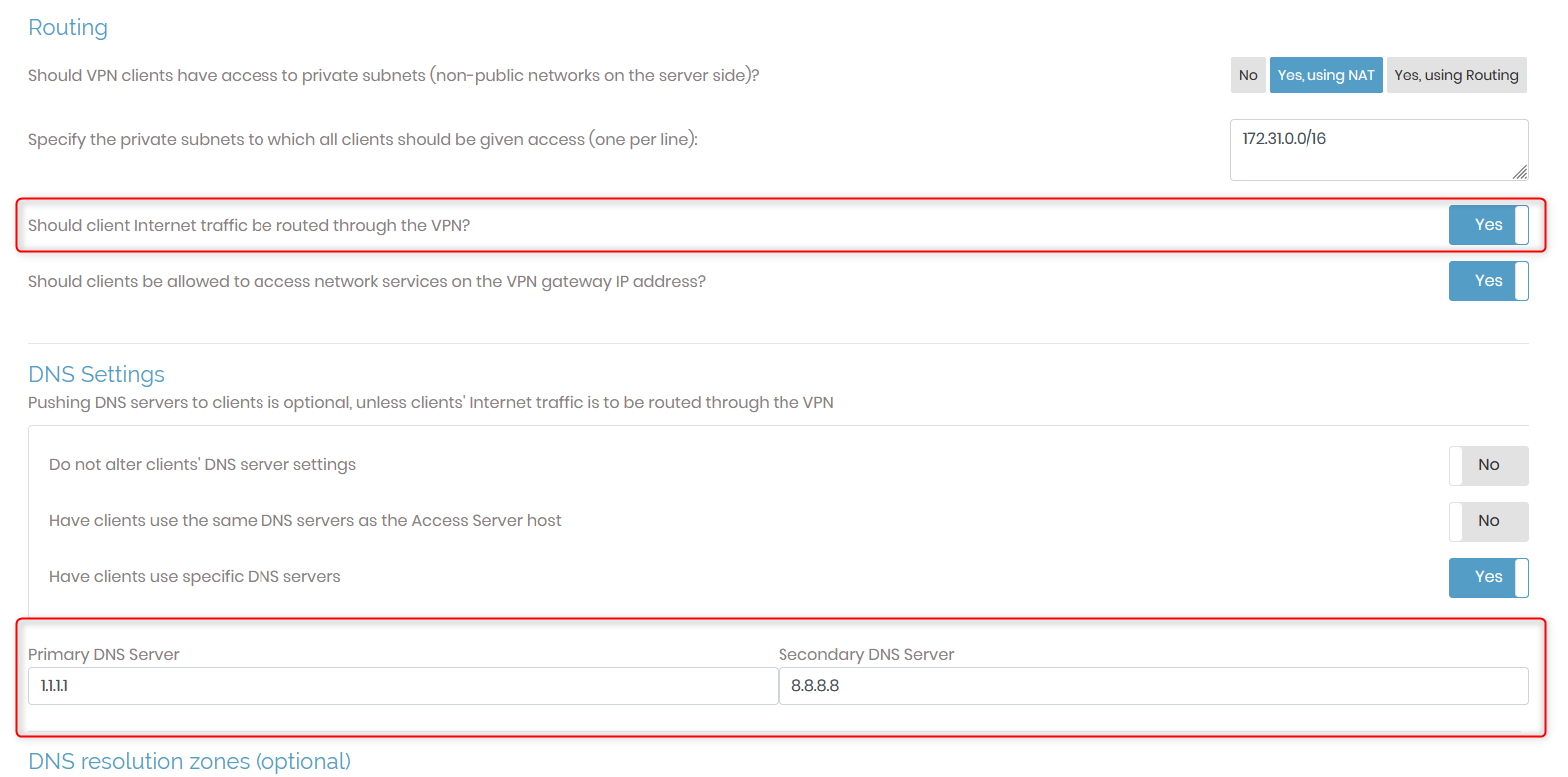
After you log into your admin portal, navigate to “VPN Settings” and toggle on the option “Should client Internet traffic be routed through the VPN?” to Yes. This will allow all the outbound traffic from your client to be encrypted and sent through the OpenVPN server before they are hit off to the internet. Additionally, we can toggle on “Have clients use specific DNS servers” and set the primary DNS server to CloudFlare DNS 1.1.1.1 and Google DNS 8.8.8.8 for improved privacy. For more information on why you shouldn’t use the default ISP DNS server, please refer to the following article:
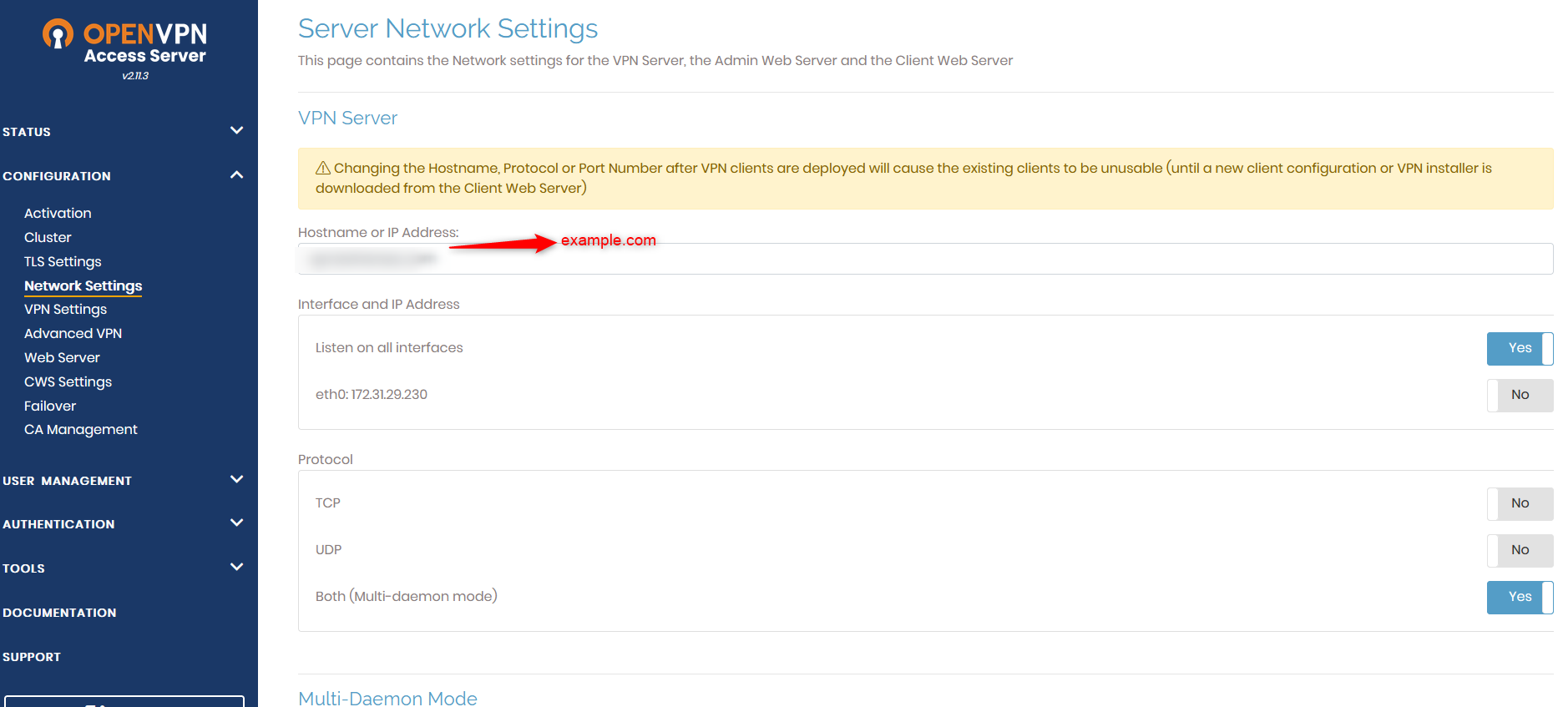
Optionally, you can also set a custom domain to the hostname and you can directly access your VPN with your domain instead of the IP address.
Please refer to the following articles on how to configure an A record for your domain:
https://openvpn.net/vpn-server-resources/setting-up-your-openvpn-access-server-hostname/
Once you configured the A record then wait for 30 minutes to an hour for the DNS record to be propagated throughout the internet.
Next, depending on your operating system, we can download a VPN client at the following URL and connect to the VPN server with the credentials we set earlier.
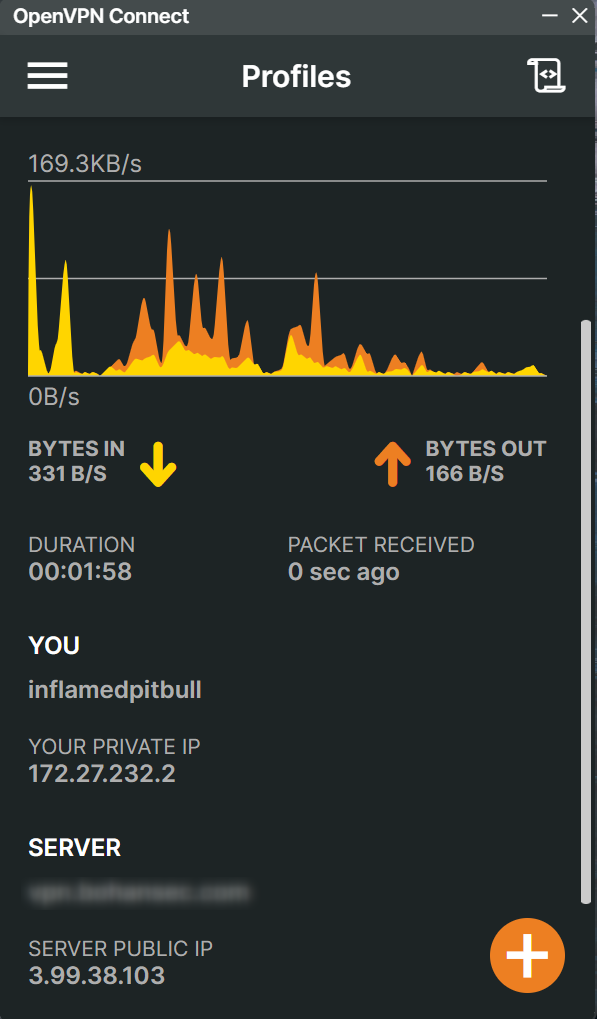
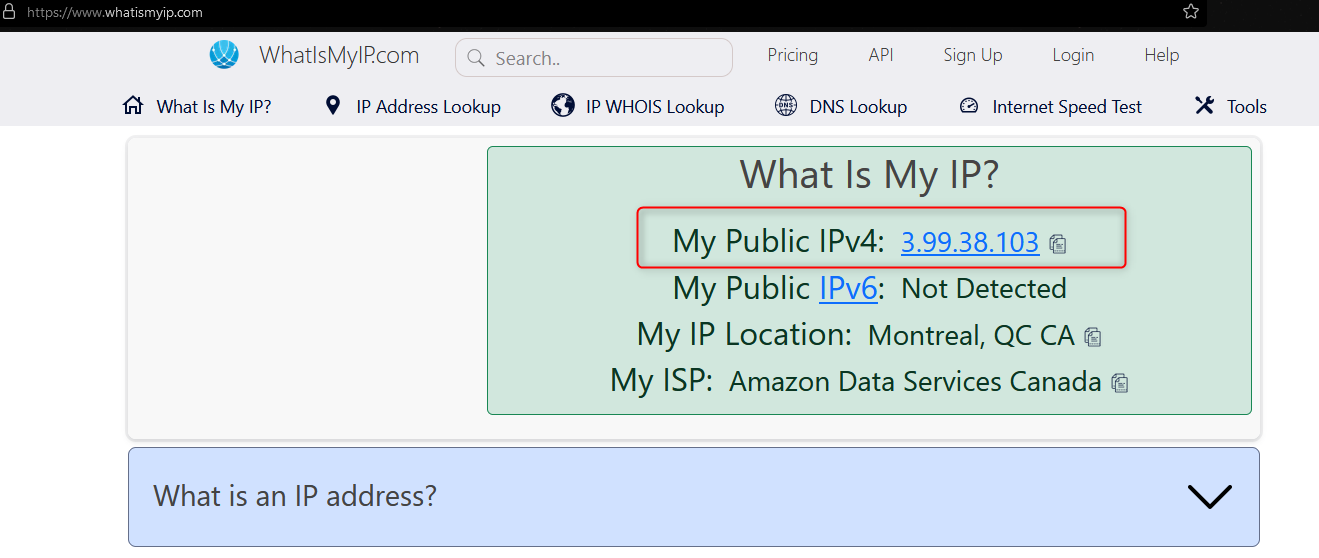
Doing a quick check on my public IP, it shows my IP is 3.99.38.103 which is the IP that I set up earlier in AWS.
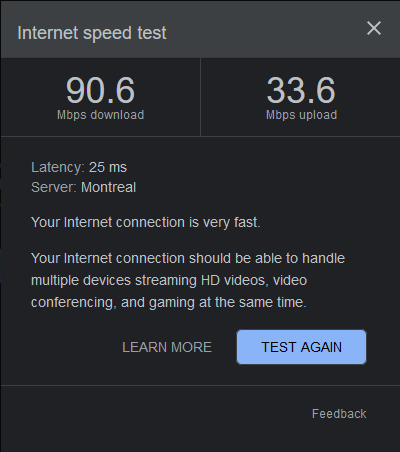
Let’s also do a speed test, while the speed dropped quite a bit compared to my original internet speed, it’s still a decent speed based on the internet test results.
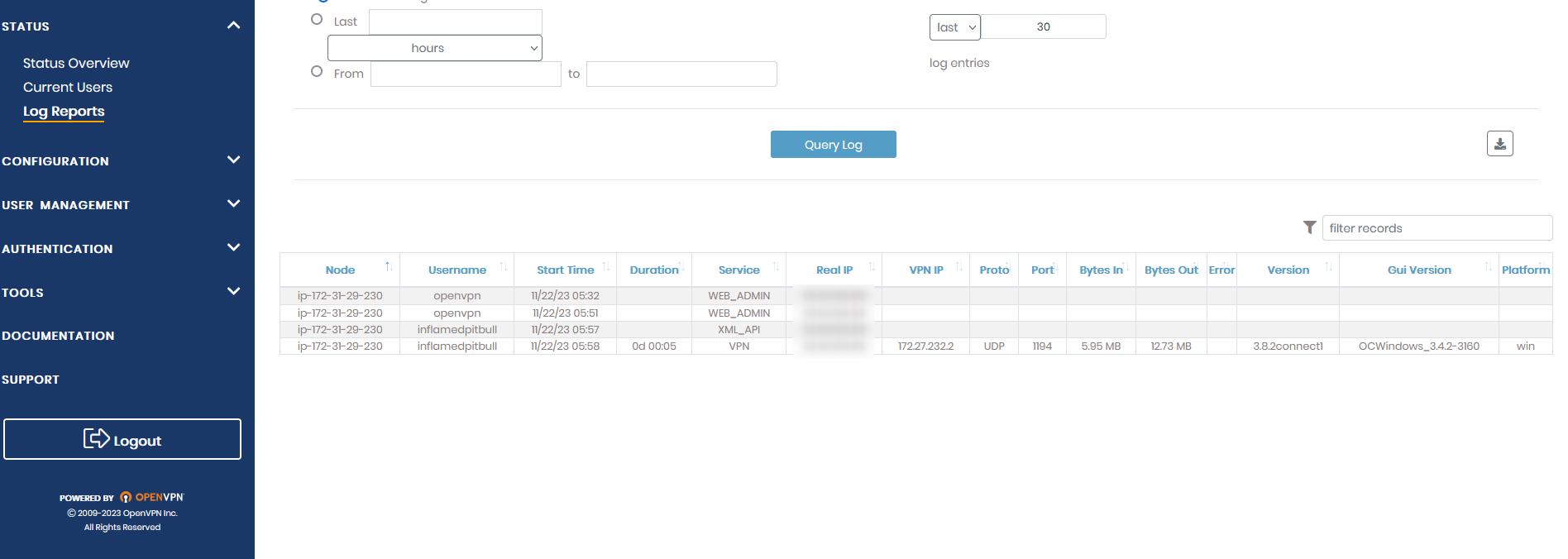
We can also track down the client’s real IP in the Log Reports section, this will be especially helpful if you want to track your user’s connection activity or look out for any suspicious connections to your VPN server.
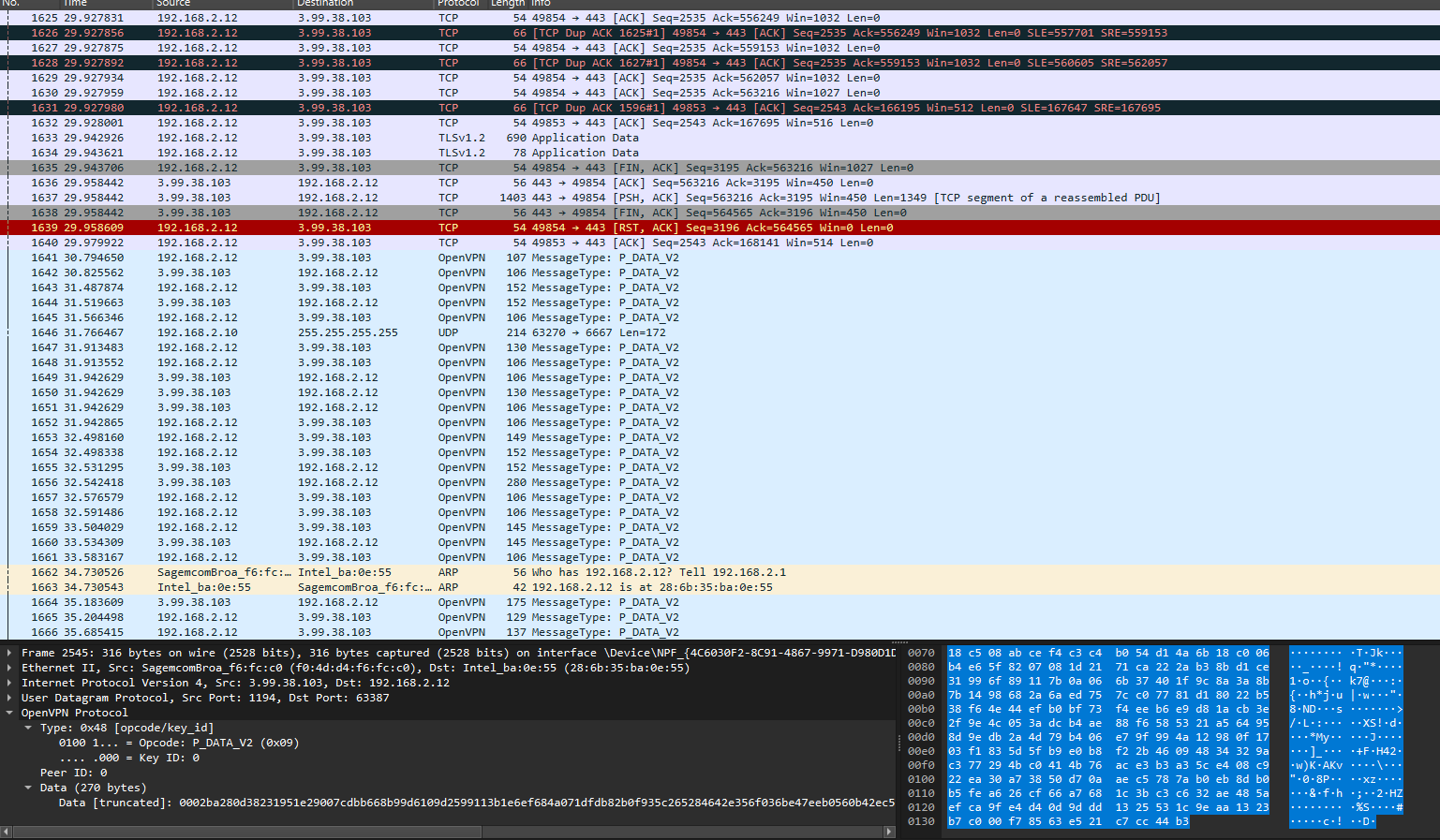
Lastly, let’s run a PCAP capture on my local network to verify my VPN connection, as you can see there are OpenVPN protocols in my network traffic which proves all my outbound traffic is being routed to my OpenVPN server.
To further harden your OpenVPN server, consider to review the following link:
https://openvpn.net/vpn-server-resources/recommendations-to-improve-security-after-installation/
Reference:
https://openvpn.net/vpn-server-resources/amazon-web-services-ec2-byol-appliance-quick-start-guide/
Thank you for taking the time to engage today. If you have any further questions or need assistance in the future, feel free to reach out. Have a wonderful day!